AI-Enhanced Security Operations
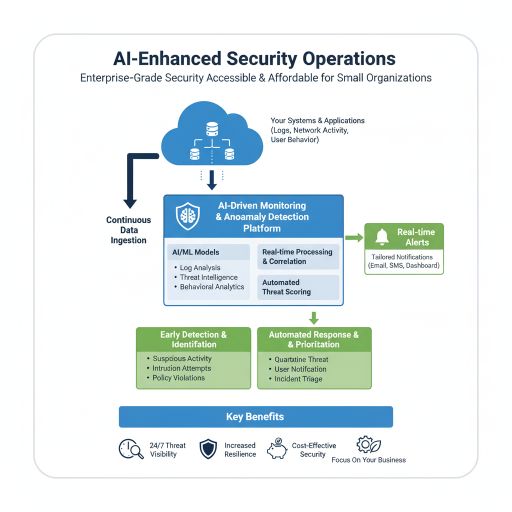
Small organizations often lack the resources for a dedicated security operations team. I fill this gap by using AI-driven monitoring and anomaly detection to provide real-time visibility into your systems and applications.
Instead of relying solely on manual oversight, I leverage intelligent tools to analyze logs, detect suspicious behavior, and identify intrusions quickly—helping you stay a step ahead of attackers. This makes enterprise-grade security accessible and affordable for smaller businesses.
Key Benefits
- Continuous log analysis powered by AI
- Early detection of anomalies and intrusion attempts
- Real-time alerts tailored to your environment
- Affordable alternative to a full SOC team
My approach reduces downtime, increases resilience, and helps you focus on your business while maintaining strong protection in the background.